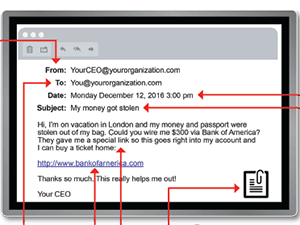
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
Biometric Authentication: The Secure Key to Protect Your Data
Discover the robust security that biometric authentication offers for your business, providing a unique safeguard with fingerprints and facial recognition that hackers can’t easily spoof.
From Insight to Action: How Data Analytics Can Help Your Business Grow
Companies of all sizes have unparalleled access to information in today’s digital era. Data created by a business may give significant insights into its operations and performance, from customer interactions and sales numbers to staff efficiency and market trends. One of the most important ways companies can use technology to …
Credential Stuffing Attack Strikes Norton LifeLock
Norton LifeLock, a leading provider of identity protection and cybersecurity services, recently experienced a data breach caused by a credential stuffing attack. Credential stuffing is a cyberattack in which a hacker uses previously compromised information from one account to access another account, website, or service. This highlights the risks of …
Create a Secure Environment for Remote Workers
Having remote workers in your business is a great way to expand cost-effectiveness and helps your business grow. But, unfortunately, many businesses have issued remote workers limited access to the network to protect important information. Knowing this, hackers are finding creative ways to access networks and steal vital information. It …
CISA Issues Warning Over Microsoft Exchange Server Vulnerabilities
Microsoft has warned that hackers are already using zero-day Exchange Server exploits to break into victims’ networks and steal data and that more attacks are likely to come. Microsoft has given more details about how the vulnerabilities have already been exploited, starting with attacks in August. In a small number …
Product Releases from Amazon’s Hardware 2022 Event
A number of exciting products were announced at Amazon’s Hardware 2022 event. These announcements include two brand-new Eero home networking products and the news that the next-generation Echo Dot devices will feature Eero capabilities. The first product is the Eero PoE 6 access point. Due to PoE (Power over Ethernet) …
Malware-as-a-Service Gaining Popularity
Malware as a Service (MaaS) has gained popularity over the past few years as a method of spreading malware. Typically, MaaS is provided at a monthly, annual, or lifetime subscription price. Once a threat actor obtains access to the malware, they can target individuals through various tactics. A relatively new …
Hackers Are Using NFT Excitement To Trick Users
Researchers from Fortinet are warning of a new threat to be on the lookout for. Right now, NFTs are all the rage. Everyone is talking about them, and many are excited about them. Hackers have been quick to take advantage of that fact, and the Fortinet researchers have stumbled across …
Microsoft Defender Adds Cross Platform Mobile Protections
Microsoft recently announced an important upgrade to Microsoft Defender. It now supports vulnerability management for both Android and iOS. The company’s announcement reads in part as follows: “With this new cross-platform coverage, threat and vulnerability management capabilities now support all major device platforms across the organization – spanning workstations, servers, …