Understanding the Dark Web The dark web represents a hidden layer of the internet, accessible only through specialized browsers and encryption tools like Tor (The Onion Router) or I2P (Invisible Internet Project). Understanding the dark web isn’t just about technical curiosity – it’s about recognizing a significant source of cyber …
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting. Critical infrastructure vulnerabilities became starkly apparent, and identity theft reached unprecedented levels. Yet, amidst the chaos, we saw strides in defensive technologies, international …
Attackers Abuse DocuSign to Send Phony Invoices
Threat actors are abusing DocuSign’s API to send phony invoices that appear “strikingly authentic,” according to researchers at Wallarm. “Unlike traditional phishing scams that rely on deceptively crafted emails and malicious links, these incidents use genuine DocuSign accounts and templates to impersonate reputable companies, catching users and security tools off …
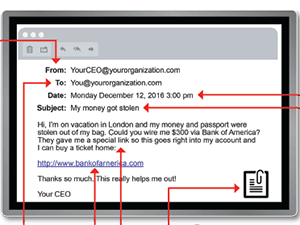
How To Recognize The Phishing Clues
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
Election-Themed Scams Are on the Rise
Researchers at Malwarebytes warn of a surge in election-themed scams ahead of November’s presidential election in the US. These attacks can be expected to increase as the election grows closer. “The lure that we have seen the most involves asking people to donate to a campaign,” Malwarebytes says. “Whether that …
8 Ways Cybercriminals Benefit from Stolen Data
Cybercriminals constantly seek to exploit stolen data for nefarious purposes. Understanding how they benefit from this data is essential for recognizing the risks and reinforcing security measures. According to the Identity Theft Resource Center’s (ITRC) 2023 Data Breach Report, the past year brought about a somber realization that cybercriminals have …
ATTENTION: Cyber Warning For Our Clients
We wanted to alert you to a cybersecurity threat our engineers have successfully mitigated for several of our clients recently. We’ve seen a rise in a specific type of cyber risk: malicious email links and attachments that appear to come from coworkers and other trusted sources like regular vendors or …
What To Look For In A Managed Service Provider: 10 Important Factors
When choosing a Managed Service Provider or MSP for your company, there are 10 important factors to consider, including: 1. Does your MSP have the IT skills and expertise to support your business? 2. Does your MSP have reliable and friendly help desk support? 3. Does your MSP provide Managed …
Why is Phishing Resistance Training So Essential?
Phishing is the gateway to many damaging cyber threats like business email compromise (BEC), ransomware and account takeover (ATO). Unfortunately, employees are inundated by phishing messages every day. They’re getting harder for users to spot thanks to technologies like generative artificial intelligence (AI). These are just a few of the …
Spam vs. Phishing: Know the Difference to Avoid a Cyberattack
How do spam and phishing relate to one another in today’s ever-evolving threat landscape? Although both terms are often used interchangeably, they represent distinct yet interconnected cyberthreats. Spam and phishing emails are sometimes difficult to tell apart due to their similarities. Here’s a clear picture of the similarities they share: …