These days, we expect giant corporations, government agencies and medical facilities to be the targets of hackers. However, golf is something new. According to a recent report from GolfWeek, the PGA’s offices have been hacked and infected with what appears to be the “BitPaymer” ransomware. That’s the same strain that …
Connecting To Airport Wi-Fi Puts Your Data At Risk
File this away under things you already knew. Coronet recently released a report entitled “Attention All Passengers: Airport Networks Are Putting Your Devices & Cloud Apps At Severe Risk,” and the news is about what you’d expect. The report was more than five months in the making. The analysts poured …
Twitter Is Getting Tough On Apps
Twitter has long had a reputation for being at the mercy of bots that have been used to sway public discourse and opinion. Often, these bots are controlled via Twitter API apps that allow the authors to automate most of their actions, such as tweets, follows, and likes. In the …
E-Mail Is A Big Threat To Your Organization
Mimecast’s 2018 “State of Email Security” report is out, and although it’s contents are hardly a surprise, the news it contains is mostly bad. For starters, it confirms what most IT professionals already know: Email continues to be a big threat for organizations of all sizes. Unfortunately, the C-Suite (CEO’s, …
Chrome Now Shows Sites Without SSL as Not Secure
There is a small but significant change from Google, with the release of Chrome 68. The updated browser will now prominently notify browsers when they surf their way to non-HTTPS websites, displaying them as “Not Secure.” This is Google’s latest step in a long campaign to try and make the …
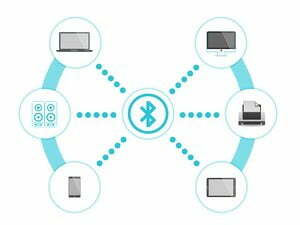
Bluetooth Vulnerability Allows Hackers To Access Devices
There’s a new Bluetooth security vulnerability to be aware of, tracked as CVE-2018-5383, and it’s a nasty one. It’s a cryptographic vulnerability that affects firmware or operating system software drivers from a number of major vendors, including Qualcomm, Broadcom, Intel and Apple. At this point, the implication of the bug …
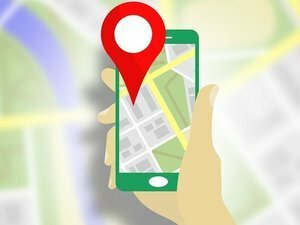
Hackers May Set Their Sights On Your GPS Next
If you’re like most people, you probably rely heavily on the GPS function of your phone. Type in an address and your phone helpfully guides you, turn by turn, to your destination. It’s one of the most often utilized features of a smartphone, and of course, the hackers are very …
New Report Shows 32 Percent Increase In Cyber Attacks
Positive Technologies has just released a new report that paints a grim picture for IT professionals. If your sense is that the number of cyberattacks are increasing, you’re not wrong. In fact, it’s probably worse than you realize. So far this year, we’ve seen a staggering 32 percent increase in …
Tip of the Week: Better Understand BYOD
There are a lot of benefits to implementing a Bring Your Own Device policy for your business. Firstly, people will be able to use the devices that they’ve purchased, and have grown accustomed to, for work. Moreover, many times they can access company information with the use of easy-to-use mobile …
Are You Ready to Adapt to Network Security Changes?
Humankind has always adapted and improved technology to make life easier, starting all the way back at fire and the wheel. Nowadays, our approach to making life easier through technology is centered around productivity and security – if we can accomplish more than before in the same amount of time, …