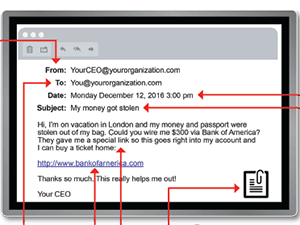
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
What To Look For In A Managed Service Provider: 10 Important Factors
When choosing a Managed Service Provider or MSP for your company, there are 10 important factors to consider, including: 1. Does your MSP have the IT skills and expertise to support your business? 2. Does your MSP have reliable and friendly help desk support? 3. Does your MSP provide Managed …
Spam vs. Phishing: Know the Difference to Avoid a Cyberattack
How do spam and phishing relate to one another in today’s ever-evolving threat landscape? Although both terms are often used interchangeably, they represent distinct yet interconnected cyberthreats. Spam and phishing emails are sometimes difficult to tell apart due to their similarities. Here’s a clear picture of the similarities they share: …
Want To Avoid Ransomware? We Can Help.
Ransomware isn’t going anywhere. Here’s why. In 1992, at the height of the Colombian drug cartels, a kilo of cocaine brought in $60,000. The average ransomware attack reaps $140,000. Consider the operating costs of a cartel. Someone must pay to grow or purchase the coca leaves, convert those leaves into …
Defending Against Wire Fraud
CEO Fraud. Business Email Compromise. Spear phishing. Wire Fraud. Pretexting. This cyberattack goes by a variety of names and may utilize a wide range of tactics, but they all come down to one thing: a malicious outsider pretends to be a legitimate boss in order to trick an unsuspecting employee …
Staying Cyber Safe On Zoom
One of our top priorities is keeping you online, whether working from a traditional office, your new home office or anywhere in between. While Microsoft offers a plethora of remote collaboration tools, we recognize Zoom is an extremely popular alternative for online meetings and educational institutions. So, we wanted to …
How To Spot And Block Dangerous Emails
Spam filters can flag suspicious emails, but ultimately you are the last line of defense in preventing attacks from cybercriminals attempting to access personal information or sensitive data. If a breach does occur, we still have your back as your managed service provider. But the best defense is a good …
Tip of the Week: How to Adjust Your Router to Improve Your Connections
Wi-Fi has been one of the single most useful innovations for the modern office. Connecting to your Internet without having to be physically connected to it via an ethernet wire has been an incredibly freeing process–one that opens up all sorts of possibilities of where (and how) you can get …
How to Best Utilize a Physical Backup
How does your business handle its on-premise, physical data backups? This is a question that you don’t necessarily have to ask yourself under pressure of a looming data loss incident. Despite the cloud being the clear victor in terms of restoration and reliability, physical data backup is still an important …
Tip of the Week: How to Reduce the Use of Paper in the Office
Paper can be incredibly expensive, especially with the quantity that a normal business goes through every single day. However, not only is it expensive on the monetary side, but also on the environmental side as well. By making some changes around your office, you can be more eco-friendly and budget-friendly …
- Page 1 of 2
- 1
- 2