Understanding the Dark Web
The dark web represents a hidden layer of the internet, accessible only through specialized browsers and encryption tools like Tor (The Onion Router) or I2P (Invisible Internet Project). Understanding the dark web isn’t just about technical curiosity – it’s about recognizing a significant source of cyber threats to your organization. Unlike the public internet that appears in everyday web searches, the dark web operates on overlay networks that provide anonymity to users and website operators alike, making it a haven for cybercriminal activity.
The impact on businesses is staggering, with cybercrime costs predicted to exceed $10.5 trillion annually by 2025. Small and medium-sized businesses are increasingly targeted, with 43% of cyber attacks specifically aimed at these organizations. The average cost of a data breach now exceeds $4.35 million, with businesses taking an average of 277 days to identify and contain a breach. The dark web serves as the primary marketplace where stolen business data, including customer information, intellectual property, and access credentials, are bought and sold.
The Hidden Digital Economy
The dark web marketplace functions like an underground version of Amazon or eBay, complete with seller ratings, customer reviews, and escrow services. This shadowy economy generates billions in annual revenue through the sale of stolen data, malicious software, and cybercrime services. Markets like STYX and Abacus operate with sophisticated payment systems, primarily using cryptocurrencies like Bitcoin and Monero for transactions.
Even small businesses are valuable targets, as criminals can bundle and sell their data alongside larger breaches or use compromised systems as launching points for other attacks. For example, a single compromised business email account can sell for $500-$1,000 on dark web markets, while complete network access credentials might command prices exceeding $10,000.
Key Players in the Dark Web Ecosystem
The dark web hosts a diverse array of threat actors, each playing specific roles in the cybercrime ecosystem. These players range from sophisticated criminal enterprises to individual opportunists, all potentially posing risks to your business operations and security.
Cybercriminal Organizations
Modern cybercriminal gangs operate with corporate-like efficiency, maintaining professional development teams, customer service departments, and affiliate networks. These organizations frequently target businesses through ransomware attacks, using a franchise-like model called Ransomware-as-a-Service (RaaS). Under this model, affiliates can rent sophisticated ransomware tools and infrastructure, making advanced cyber attacks accessible to criminals with limited technical skills.
Notable examples include groups like Conti, which generated over $180 million in ransom payments in 2021, and LockBit, responsible for approximately 30% of all ransomware attacks in 2022. These groups often provide detailed documentation, technical support, and even guaranteed results to their affiliates.
Initial Access Brokers
Initial Access Brokers (IABs) specialize in compromising business networks and selling that access to other criminals. These actors exploit various vulnerabilities, from unpatched software to weak passwords, creating persistent access points that can be sold multiple times to different criminal groups. Common attack vectors include:
- Exploiting Remote Desktop Protocol (RDP) connections
- Compromising Virtual Private Network (VPN) credentials
- Utilizing phishing campaigns to harvest login credentials
- Exploiting zero-day vulnerabilities in business applications
Once an IAB compromises your network, they may advertise access on dark web forums, potentially leading to ransomware attacks, data theft, or other malicious activities. Prices for network access typically range from $1000 to $30,000, depending on the organization’s size and potential value.
Malicious Insiders
Criminal organizations actively recruit employees through dark web channels, offering substantial payments for internal access or sensitive data. These insider threats can be particularly dangerous as they bypass many traditional security measures. Warning signs might include:
- Unusual file access patterns or data downloads
- Off-hours network activity
- Employees displaying sudden interest in areas outside their normal responsibilities
- Unexplained changes in financial circumstances
- Reluctance to take vacation time or share work responsibilities
Dark Web Marketplaces and Communication Channels
Cybercriminals utilize various platforms to conduct their operations, ranging from traditional dark web markets to unexpected communication channels.
Traditional Dark Web Venues
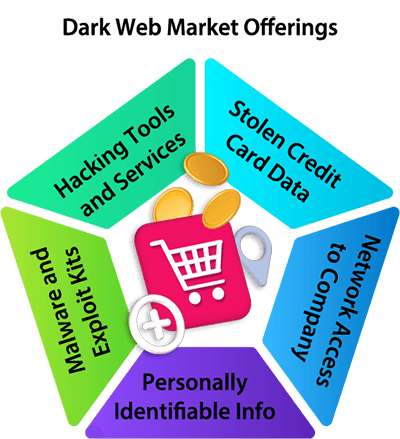
Dark web marketplaces operate similarly to legitimate e-commerce sites, complete with search functions, customer reviews, and secure payment systems. These markets specialize in selling:
- Stolen credit card data and financial information
- Corporate network access credentials
- Personally identifiable information (PII)
- Malware and exploit kits
- Hacking tools and services
Additionally, ransomware groups maintain “leak sites” where they publish stolen data to pressure victims into paying ransoms. These sites often feature countdown timers and sample data to create urgency.
Unexpected Platforms
Cybercriminals increasingly use mainstream platforms like Telegram, Discord, and even gaming chat systems to coordinate activities and sell illegal goods. These platforms offer easy access, encrypted communications, and the ability to quickly create and abandon channels when needed. Some groups have even begun using legitimate business collaboration tools like Slack or Microsoft Teams, accessed through compromised corporate accounts.
Protecting Your Business from Dark Web Threats
Implementing robust security measures is crucial for protecting your business from dark web threats. This includes maintaining strong access controls, regularly updating software, and conducting thorough employee security training.
Prevention Strategies
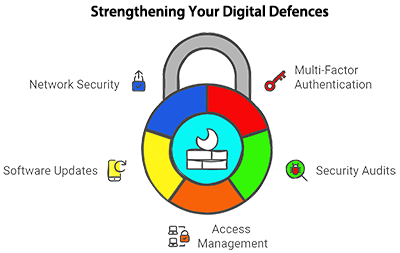
Establish comprehensive security protocols including:
- Multi-factor authentication for all user accounts
- Regular security audits and penetration testing
- Strict access management policies using the principle of least privilege
- Regular software patching and updates
- Network segmentation and monitoring
- Encrypted backup systems with offline copies
- Email filtering and web security gateways
Train employees to recognize social engineering attempts and maintain good security practices. Implement zero-trust security principles, assuming no user or system is automatically trustworthy.
Monitoring and Response
Utilize dark web monitoring services to detect leaked credentials or data related to your organization. Develop and maintain an incident response plan that outlines specific steps to take when a security breach is detected. Essential components include:
- Designated response team members and responsibilities
- Communication protocols and escalation procedures
- Data backup and recovery processes
- Legal and regulatory compliance requirements
- Customer notification procedures
- Post-incident analysis and improvement strategies
Partner with cybersecurity professionals to ensure your security measures remain current and effective.
Taking Action: Next Steps for Business Leaders
You must take proactive steps to protect your organization from dark web threats. Begin by conducting a thorough security assessment and implementing basic security measures immediately.
Security Assessment
Start with a comprehensive evaluation of your current security posture. Identify potential vulnerabilities in your systems, processes, and human elements. Work with security professionals to develop a prioritized plan for addressing identified weaknesses. Key assessment areas should include:
- Network infrastructure and access controls
- Data storage and protection measures
- Employee security awareness and training programs
- Incident response capabilities
- Third-party vendor security
Building a Security-First Culture
Establish regular security training programs for all employees. Develop and enforce clear security policies that address modern threats. Create a culture where security awareness is part of everyday operations, not just an annual training requirement. Regular activities should include:
- Monthly security awareness updates
- Simulated phishing exercises
- Security policy reviews and updates
- Recognition programs for security-conscious behavior
- Regular security assessment meetings
The dark web poses significant risks to businesses of all sizes, but understanding these threats is the first step toward protecting your organization. By implementing robust security measures and maintaining vigilance, you can significantly reduce your exposure to dark web threats and better protect your business assets.






